Configuring Authentication
Authentication is the process of validating user credentials. Individuals who use WebFOCUS may have user IDs and passwords managed by other systems. WebFOCUS Managed Reporting and the Reporting Server can each be configured to authenticate users to an external security system, or to trust that authentication has already taken place. Users benefit because they do not have to sign in multiple times or manage separate user ID/password combinations. If a user signs in to WebFOCUS with credentials from an outside security package, the package provides some type of authentication confirmation to the WebFOCUS Client or the Reporting Server. This information may be in the form of a browser cookie or a logon ticket and may be needed by the Reporting Server in order for it to access and retrieve the data required by the WebFOCUS application.
Depending on your operating environment, user credentials can be validated by:
- The operating system on which the server is running (OPSYS security).
- A list of users stored in the server file named admin.cfg (PTH security).
- An LDAP or Active Directory repository (LDAP security).
- A DBMS (DBMS security).
- A custom user-supplied procedure (CUSTOM security).
Multiple security providers can be configured. You can configure additional providers using the Web Console Access Control page.
Configuring a New Security Provider
Security providers must be configured from the Web Console Access Control page.
To switch to security provider LDAP, DBMS, or CUSTOM, you first need to add a new provider under the appropriate security provider on the Access Control tree. When you add a new provider, the server updates configuration file edaserve.cfg with provider blocks named LDAP_PROVIDER, DBMS_PROVIDER, or CUSTOM_PROVIDER. These blocks are inserted with all attributes that apply to the provider type between BEGIN and END dividers.
Security provider PTH is configured during installation of the server and is the default security provider when a newly installed server is started. A server administrator can configure and activate other security providers.
The OPSYS security provider is always on the list of providers. In order to make it an active provider, the server must be authorized (privileged) to start with security OPSYS. There is no need for the additional step of creating a new provider as is needed for LDAP, DBMS, and CUSTOM providers. By default, the effective server administrator ID shown on the Activate Providers page is the server administrator ID. You can change this using the Access Control Settings page. Once the server is installed, you can start adding new PTH users and PTH groups, and you can assign PTH users to PTH groups.
Security provider CUSTOM supports using non-standard security storage. You can create DBMS tables to store users, groups, and passwords. You must then write procedures to read these tables and perform the basic security tasks. This security mechanism has to be created prior to configuring the CUSTOM security provider and must be available when the CUSTOM provider is added to the server provider configuration. It must perform the following standard security tasks:
- Retrieve the user ID and its password to authenticate the user on connecting to the server.
- Retrieve the list of users and groups on user and group registration.
- Retrieve the list of users in each group.
- Retrieve user membership in all available groups.
Once the provider is added, you can change security providers from the Access Control page. Right-click the Security Providers folder and select Activate Providers to switch to a newly added provider. At this point, edaserve.cfg is updated with the security_provider attribute that specifies the provider name.
Multiple security providers can be configured. When you configure OPSYS as one of multiple security providers:
- The server has to be authorized to run security OPSYS, and it needs to have a valid OS user ID and password for starting an agent.
- In a multi-provider security environment that includes an OPSYS security provider, other provider names should not match any domain name reachable by the OPSYS provider.
The Access Control Settings page lets you enter valid OS credentials.
When you configure multiple providers, you choose one to be primary on the Access Control Activate Providers page. Drop-down lists are available for assigning the other providers as secondary providers or inactive. The primary provider defines the security under which the server is running:
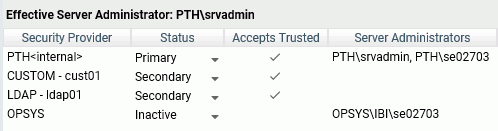
During connection to the server, all provider users are connected with a two-part user ID consisting of the provider name and the user ID, for example, MyLDAP\User1 or MyDBMS\User2, where MyLDAP or MyDBMS is the name of a configured secondary provider.
This naming convention is also used when users and groups are registered to server roles. Users and groups are registered with a two-part name. If the PTH provider is a secondary provider, PTH users and groups are registered (and used on connection) as PTH\userid and PTH\groupid.
Example: Security Provider Blocks in edaserve.cfg
The following is an example of a security_provider attribute and security provider block for starting the server with security LDAP (provider name MyLDAP):
security_provider = MyLDAP LDAP_PROVIDER = MyLDAP BEGIN ldap_host = ldaphost ldap_port = post ldap_secure_connection = n ldap_user_base = dc=ibi,dc=com ldap_user_scope = subtree ldap_user_class = person ldap_user_attribute = uid . . . END
The following is an example of a security_provider attribute and security provider block for starting the server with security DBMS (provider name MyDBMS):
security_provider = MyDBMS DBMS_PROVIDER = MyDBMS BEGIN security_dbms = MSSSQL security_connection =CON01 END
Configuring OPSYS Authentication
|
Topics: |
When security provider OPSYS is configured, the user credentials from the client connection are authenticated by the native security system of the operating system. The server then allocates a data access agent that impersonates the user so that access to files or other objects is controlled by the native system.
Profiles for operating-system users are supported on all platforms. On Windows, Active Directory groups are supported based on the win_primgroup_adsi setting.
Details about OPSYS security requirements are provided in the Server Installation manual, where specific sections are provided for each platform. Refer to this manual for installation instructions and platform-specific setup steps. The following is a summary of the OPSYS requirements:
- On UNIX, the startup tscom300 executable must have root setuid authority.
- On Windows, the
server must be started as a service under SYSTEM account (Administrators
Group authority) or as a user ID with Windows Administrator authority.
On Windows, the Server Administrator password is required for this security provider. If the password is not provided in the configuration, the server starts in safe mode and displays a message to that effect. Multiple administrators are allowed. For more information on creating server administrators and other roles, see Registering Users and Groups in a Role.
- On z/OS, the MVS load library must be APF-authorized, and for HFS deployment, certain HFS executables must be given +a authorization.
- On IBM i (formerly known as i5/OS), the ownership of certain library files must be changed to have QSECOFR ownership and, therefore, authority.
- On OpenVMS, the account starting the server must have a specific set of privileges to have proper authorities.
Note that some system specific settings in the edaserve.cfg file are provided to allow further adjustments of the authentication mechanism. Those relevant for some UNIX systems are:
- require_logon_privilege (AIX only. Allows no sign-in IDs to access the server.)
- update_security_db (AIX and HP-UX only. Registers failed sign-in attempts.)
For Windows systems, the logon_method setting (for interactive, network, or batch) is relevant to explicit connections.
Note: For more information on limiting user access to the Web Console, see Configuring General Server and Web Console Actions.
Preventing Unsecured Server Starts After Upgrades
If the environment variable EDAEXTSEC is explicitly set to OPSYS, and the server fails to start because it lacks system privileges to start configured for an OPSYS security provider, the server start aborts and error messages are written to the edaprint log file.
This feature prevents an unsecured server start after a software upgrade if any of the required post-upgrade reauthorization steps are missed on a UNIX, IBM i, or z/OS HFS deployment. This is not applicable to other platforms. The setting may be placed in any normal server start-up shell or profile that a site is using or in the server edaenv.cfg configuration file. The messages vary slightly by platform.
The edaprint messages are:
Configured security is 'ON' as set by EDAEXTSEC variable.
Server has no root privilege. (UNIX)
Server is not APF-authorized. (z/OS HFS)
TSCOM300.PGM has no QSECOFR authority. (IBM i)
Workspace initialization aborted.
(EDA13171) UNABLE TO START SERVER
Using Password Phrases for Authentication on z/OS
|
How to: |
Starting with z/OS 1.8, IBM introduced password phrases which can be used for authentication, and starting with z/OS 1.10 password phrases can be used for TSO Logon as well. Password phrases can be from 14 to 100 characters long.
z/OS IDs can have both a password (1 to 8 bytes) and a passphrase (from 14 to 100 bytes). The two forms of credentials are independent. Changing one does not change the other. The server recognizes the type of credential being presented by its size (sizes between 9 and 13 are invalid on z/OS).
No special configuration is needed to enable password phrases.
When a user logs into the Web Console, there are two possible ways they can change their passwords or passphrases:
- On the initial Web Console Logon page. This option is disabled by default. For more information on enabling this option, see How to Change Passwords on the Web Console Logon Screen.
- After the initial logon, by choosing Change Password on the My Console menu. A new screen opens with three separated fields (old password, new password, and confirm new password).
Procedure: How to Change Passwords on the Web Console Logon Screen
By default, passwords cannot be changed on the Web Console Logon page because the following parameter is in effect:
password_change_wclogin = n
To enable the option to change passwords when logging into the Web Console:
- Select Access Control from the Web Console menu bar.
- Right-click Access Control on the tree and select Settings from the context menu.
- Change the value of the password_change_wclogin parameter to y.
On the same configuration page, you can change the delimiter used to separate the user ID from the password or passphrase to any valid character accepted by the operating system. By default, the delimiter is a comma:
password_change_delimiter= ,
Once the option to change passwords on the Web Console Logon page is enabled, users can change their passwords or passphrases by entering the following in the password field of the Web Console Logon page (if the password delimiter has been changed, use that character between the old and new passwords instead of the comma):
old_password,new_password
When password_change_wclogin = y, passwords and passphrases cannot contain the password delimiter character.
When password_change_wclogin = n (the default), the setting for password_change_delimiter is ignored, and passwords can contain all valid characters allowed by the operating system.
Configuring Linux and AIX Pluggable Authentication Modules (PAMs)
In a Linux or AIX environment, OPSYS security can be configured to use Pluggable Authentication Modules.
- Select Access
Control on the Web Console sidebar.
The Access Control Page opens.
- Right-click the OPSYS security provider and select Properties from the context menu.
- Select y from
the security_pam drop-down list.
This parameter is only applicable for the Linux and AIX operating systems. The parameter defines if the server uses the Pluggable Authentication Modules mechanism to implement security. If y, the server uses PAM calls, if n the server uses native UNIX security calls.
- Click Save and Restart Server.
Using Kerberos for Single Sign-On on Linux
A server started with security provider OPSYS can be configured for Kerberos connections.
To implement the single sign on Kerberos security:
- On the Access Control page, right-click the OPSYS provider,
and select Properties from the context menu.
The OPSYS Security Configuration page opens.
- In the krb5_srv_principal * field, enter your server principal used for Kerberos security.
- Click Save.
The edaserve.cfg file is updated with this attribute.
- On the Workspace page, expand the Special Services and Listeners folder, right-click TCP/HTTP, and select Properties of TCP.
- Check SECURITY=KERBEROS.
- Click Save and Restart Listener.
The odin.cfg file is updated with this attribute.
When the server is started, a user can connect to the Web Console from Internet Explorer without a prompt for user ID and password. The Login Info shows connection type Kerberos. The connection is done using the Kerberos ticket from the browser. The connected user ID is derived from this ticket.
Connection to the server requires that there is a local OPSYS user ID with the same name as the Kerberos user ID on the operating system running the server. This user ID is used for tscom3 process impersonation.
If a user signs off from the Kerberos connection, the user can make explicit connections with the local Unix user ID and password. Connection with another Kerberos user ID as an explicit connection will not work.
Configuring PTH Authentication
|
Topics: |
|
How to: |
By default, the server installation process establishes PTH security with a PTH server administrator user ID and password. If you deleted the PTH server administrator ID, you can reconfigure PTH security.
The PTH security provider only controls access to the Web Console. When the server is configured for this security provider, there is no impersonation by data agents or authentication of a non-Web Console connected user. From the operating system point of view, all server processes run as a single user ID, and access to the Web Console is controlled by authenticating names against those defined in the admin.cfg file unless authenticate_all_pthuser is set to y. The setting is available on the PTH Security Configuration page, which can be accessed by right-clicking PTH in the Security Providers folder on the Access Control resources tree.
You must configure the Server Administrator password before starting a server configured for a PTH security provider, either by providing it at installation time or by configuring it in the Web Console. For details, see Registering Users and Groups in a Role.
The PTH security provider supports profiles for users and groups on all platforms.
Note: For more information on limiting user access to the Web Console, see Configuring General Server and Web Console Actions.
Procedure: How to Configure Password Properties for a PTH Security Provider
When the Server Administrator creates or updates a user under a PTH security provider, by default the password never expires, can be any length, and is not case-sensitive.
The Server Administrator can configure a new or existing user password to expire after a specified number of days, can set a minimum length for passwords, can enable case-sensitive passwords, and set other password properties.
- To
assign an expiring password, click Access
Control.
- Right-click PTH and click Manage Users/Groups.
The PTH Users and Groups Management page opens.
- If the user does not yet exist, create the user. Then,
click Properties on the menu bar.
By default,Password never expires is checked.
- Uncheck Password never
expires.
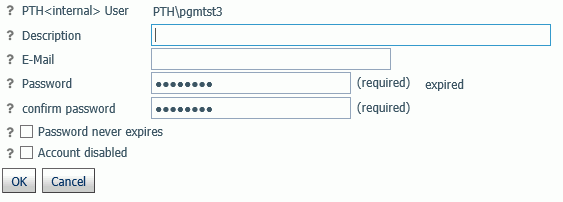
When the password expires, the user gets a password expired message on the logon screen and is provided with a New Password field in order to enter a new password.
At this time, the new password and new password change date are recorded in admin.cfg.
Note that changing the password by selecting Change Password from the My Console menu also resets the password change date.
- Click OK.
The current date is saved in admin.cfg as admin_passdate for this user. This is the last password change date.
- Click Save.
- Optionally, configure a warning message to begin displaying a specified number of days before the password expires, as described in Sign-in Password Expiration Warning.
- Right-click PTH and click Manage Users/Groups.
- To configure other password properties:
- Right-click the PTH Security Provider and click Properties.
The Security Configuration PTH page opens
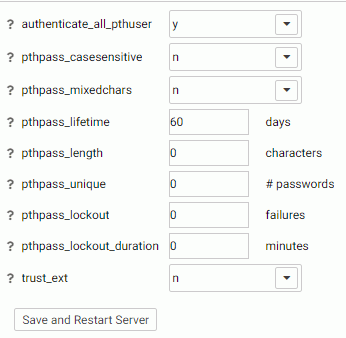
- Set the following properties.
- authenticate_all_pthuser. Valid values are y and n. Defines whether the server will authenticate all connections, including Basic Users, to the Web Console. The default value is y.
- pthpass_casesensitive. Valid values are y and n. Defines whether authentication of passwords will be case sensitive. The default value is n.
- pthpass_mixedchars. Valid values are y and n. Defines what characters should be required in a password. If the value is y, a password must contain at least one special character, one numeric character, and one letter (one uppercase and one lowercase letter, if pthpass_casesensitive is set to y). The default value is n.
- pthpass_lifetime. Defines the maximum password lifetime in days. Zero (0) means no expiration. The default is 60.
- pthpass_length. Defines the minimum number of characters that must be present in a password. Zero (0) means no minimum requirement. Zero is the default value.
- pthpass_unique. Defines the number of password cycles during which a password cannot be reused. The value zero (0) means passwords can be reused. Zero is the default value.
- pthpass_lockout. Defines the number of failed sign-in attempts that will cause a user account to be locked. The value zero (0) means no limit. Zero is the default value.
- pthpass_lockout_duration. Defines the number of minutes that a locked-out account remains locked out before automatically becoming unlocked. The value zero (0) means that the account will be locked out until an administrator explicitly unlocks it. Zero is the default value.
- trust_ext. Valid values are y and n. Specifies whether the server should accept trusted client connections. If there are multiple security providers, some may allow trusted connections and some may not. In these cases, if the trusted connection is made using a provider without the ability to accept trusted connections, the user will get an authentication error. The default is y for security OPSYS (except Windows security OPSYS), n for Windows security OPSYS and all other security providers.
- Click Save and Restart Server.
- Right-click the PTH Security Provider and click Properties.
Disabling a PTH Security Provider Account
You can disable an account that is registered in admin.cfg under the PTH security provider in order to prevent a user from signing in to the server with that account.
To disable a PTH account:
- Right-click PTH under the Security Providers folder,
and select Manage Users/Groups from the context
menu.
The PTH Users and Groups Management page opens, listing all registered users on the left, and all registered groups on the right.
- Select a user and click Properties.
The PTH User properties dialog box opens.
- Click Account disabled as shown in the
following image:
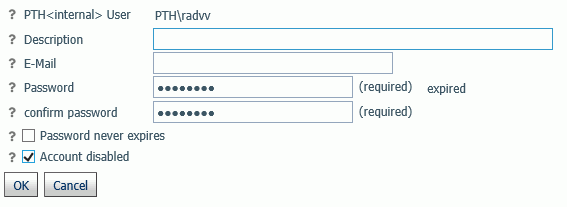
- Click OK.
An x is displayed in the Disabled column for that user on the PTH Users and Groups Management page.
- Click Save.
Configuring DBMS Authentication
With a DBMS security provider, there is no impersonation by data agents, but connection credentials are authenticated against a configured DBMS. This technique is called password passthru, as user IDs and passwords supplied by the client are passed to the DBMS for authentication.
A DBMS security provider supports profiles for users on all platforms. Profiles for groups are not supported.
Note: For more information on limiting user access to the Web Console, see Configuring General Server and Web Console Actions.
Configuring LDAP Authentication
With an LDAP (Lightweight Directory Access Protocol) security provider, there is no impersonation by data agents, but connection credentials are authenticated against the established directory services. From the operating system point of view, all server processes run as a single user ID.
An LDAP security provider is presently supported on Windows, UNIX, IBM i, and the Unified Server (HFS and PDS deployments).
An LDAP security provider supports profiles for LDAP users and LDAP groups.
Note: For more information on limiting user access to the Web Console, see Configuring General Server and Web Console Actions.
Configuring Custom Authentication
|
Topics: |
CUSTOM security providers are used when the installation maintains non-standard repositories for users and groups, that is, when the standard methods like OPSYS and LDAP do not apply. An example of such a setup can be having RDBMS tables containing valid user IDs and their encrypted passwords, and also containing the mapping of users to groups. The customer may chose to access these tables using SQL SELECT statements, SQL Stored Procedures, or Web Services. Typically these methods already exist and are used by other non-Information Builders components.
To enable the custom server security provider, the administrator needs to provide code that allows the server security module to perform these tasks:
- Authenticate the user based on user ID and password.
- Obtain all groups for a user (used at run time).
- Obtain all groups in the system (used for administrative actions).
- Obtain all users for a group and all users in the system (used for administrative actions).
The code for performing these tasks is written in the WebFOCUS language as TABLE FILE or SQL SELECT commands against the synonyms representing the SQL table, SQL Stored Procedure, or Web Service. The code can be debugged by running the server with security OFF and running the glue code from application folders. Once debugged, the code is deployed in EDACONF/catalog/custom, and the CUSTOM provider made active.
A tutorial sample called WebFOCUS - Custom SQL Security Provider is available that creates examples of user and group storage and custom procedures that can be used as prototypes. To generate a tutorial, right-click an application on the Application page, point to New, and click Tutorials from the context menu.
Encoding Passwords for a Custom Security Provider
You can configure Custom Provider authentication to encode passwords so that they cannot be viewed when they are passed as parameters to the authentication procedure.
- On the Access Control page, right-click a Custom Security
Provider and select Properties from the context
menu, or right-click the CUSTOM folder and select New from
the context menu.
The CUSTOM Security Provider Configuration page opens.
- Select y from the cust_hashpasswd drop-down list.
- Click Save.
When a user is authenticated, the server will send SHA-256 hashed passwords to the authentication procedure. This means that the passwords will be transformed into values that will be unusable for signing in to the Web Console and server. The hashed values have to be stored as passwords in the SQL database being used for authentication. As an alternative, you can create a utility called from the CUSTOM provider authentication procedure that decodes hashed passwords before sending a request to the SQL database for authentication.
Authenticating Users Across Multiple Security Providers
The Reporting Server can search across multiple LDAP sources, DBMS providers, an OPSYS provider, and a PTH server when authenticating users.
When authenticating or assigning privileges for a provider that is not the primary provider, the user ID is a two-part name consisting of the provider name and the user ID:
provider\userid
The authentication is done based on a two-part name.
The Server Administrator can add and remove security providers from the list at any time.
For instructions on configuring PTH and LDAP security providers, see Configuring Authentication or Configuring Authentication.
Enabling Trusted Connections
You can enable trusted connections separately for each security provider.
You can configure a security provider to accept trusted connections by setting its trust_ext value to y.
- Right-click a security provider on the Access Control tree
and click Properties on the context menu.
This example shows a PTH security provider, but the same setting
is available for all security providers.
The Configuration page for that security provider opens.
- From the trust_ext drop-down list, select y.
This setting is available for all types of security providers.
- Click Save and Restart Server.
Identifying a Default Provider for Trusted Groups
When multiple security providers are configured, one must be identified as the default provider for trusted connections when WebFOCUS or other client software sends a trusted group ID without a security provider to the server.
To set the default provider for trusted groups:
- On the Access Control page, click Access Control on
the ribbon, or right-click the Access Control folder
and select Access Control from the context menu.
The Access Control Settings page opens, as shown in the following image.
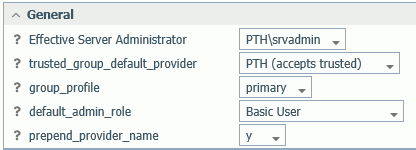
- You can select a security provider that accepts trusted connections from the trusted_group_default_provider drop-down list. You must select a provider that is configured to accept trusted connections. You can also enter IP addresses to be mapped to a specific provider, if no provider name is supplied by the client.
Setting an Anonymous User ID
An authorized server administrator can set an anonymous user ID that can access the Web Console when the user ID/password fields on the Web Console sign in screen are blank and the user clicks Sign in.
This anonymous user ID provides the ID and, in turn, the user rights for the Web Console and the server. Further configuration for the anonymous user can be achieved by creating a user profile for the anonymous user ID. If an anonymous ID matches a user in the admin.cfg list, the applicable role and privileges are applied.
Note: On Windows, for security provider OPSYS only, you must turn IWA security off to use this feature. From the Workspace page, open the Special Services and Listeners folder, right-click TCP/HTTP, and select Properties. Click the Security IWA check box to deselect it.
- Log on to the Web Console using a user ID that has server administration rights.
- Click Access Control.
- Click Access
Control on the ribbon.
The Access Control Settings page opens.
- Enter a user ID in the anonymous_id field.
- Enter a password in the anonymous_pass field and repeat it in the confirm password field.
- Click Apply and Restart Server.
Configuring User Password Settings
|
Topics: |
|
How to: |
You can configure the following password settings for any security provider:
- View or change the password separator character.
- Enable users to change passwords from the Web Console sign in page.
- Control the start time of warning messages on operating systems that support password expiration.
Procedure: How to View or Change the Password Separator Character
When an application has the option to change a user password, the old and new passwords are sent to the server using a separator character (by default, a comma). For example:
old_password,new_password
The separator character is defined by the password_change_delimiter field. The separator needs to be reset if the current separator character is contained in the password itself or if it is allowed by the server.
This feature is not supported when Security is OFF.
- Click Access Control on the sidebar to go to the Access Control page.
- Click Access
Control on the ribbon.
The Access Control Settings page opens.
- In the password_change_delimiter field,
enter a single character to use as the delimiter between an old
and new password. (The default character is a comma.)
Note that you cannot use the designated password_change_delimiter character in a password.
- Click Apply and Restart Server.
Procedure: How to Enable Password Changes From the Web Console Sign-in Page
A Server Administrator can allow users to change their password from the Web Console sign-in page. By default, users cannot change their passwords from the Web Console sign-in page.
- Sign in to the Web Console with Server Administrator privileges.
- Click Access Control on the sidebar.
- Click Access
Control on the ribbon.
The Access Control Settings page opens.
- Select y in the password_change_wclogin field. The default is n.
- Click the Apply and Restart Server button.
Sign-in Password Expiration Warning
On Operating Systems that support password expiration, you can specify that a warning message be displayed a specified number of days prior to the expiration date. The message will appear after the initial sign-in screen. You must then click the Continue button to open the Web Console. Users can employ standard tools to change their passwords before expiration occurs.
Note: The password expiration warning is supported only on operating systems where IDs are configured to expire, and this extended security feature is active for the user ID. However, expiration warning is not currently supported on Windows platforms.
How to Initiate Notification of an Imminent Password Expiration
- Click Workspace on the sidebar.
- In the resources tree, expand the Special Services and Listeners folder, then right-click TCP/HTTP and select Properties or HTTP from the context menu. The Listener Configuration pane opens.
- Expand the Sessions Control group.
- In the PASS_EXPIRE_NOTIFICATION field, enter the number of days prior to expiration that you want the warning to begin to appear when a user whose password is about to expire logs in.
- Click Save and Restart Server.
| WebFOCUS | |
|
Feedback |