Enabling Security in Magnify With Lucene
|
Topics: |
When using the Lucene search engine, Magnify provides a Java-based Security API that enables record-level security, whereby users are granted access to data on an individual basis. The rules for data access are defined in the Magnify Security plug-in, which is called once a secure record in the Lucene index is triggered. A Lucene index can contain both public and secure records. Secure records are tagged with security parameters that specify the name of the Magnify Security plug-in and other parameters that are used to define the security rules for accessing an individual record. This flow is illustrated in the following image:
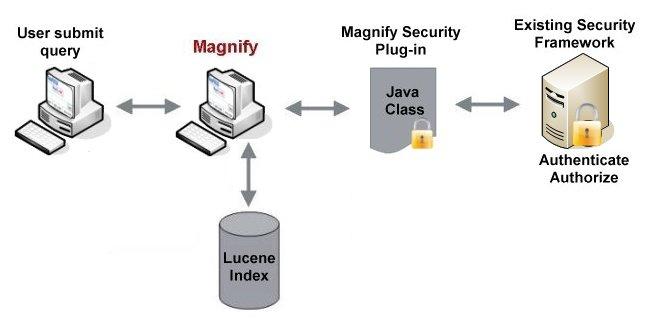
Using the Security API, Magnify can integrate with an existing security framework and be extended to provide important security features, such as:
- HTTP Cookie Verification. Magnify can use existing cookie information to authenticate and authorize a user. The cookie name is specified in the WebFOCUS Administration Console.
- Single Sign-on Integration. Magnify integrates with existing single sign-on frameworks. Authentication passes to Magnify and is used to authorize user access to information.
- Hide Parts of Results. Some security rules will allow you to see a search result, but only grant you authorization to specific pieces of the search result. For instance, Salary Range is a category used to filter the result set. If you are not allowed to see manager salaries and you clicked the range matching the salary of your manager, you will not find your manager in the search results. On the other hand, if you filter on the title of your manager, you will find your manager in the search results. Magnify security allows for hiding parts of search results, including the metadata.
- Present Alternate Result Rendering. Sometimes you may be restricted from viewing a search result, but you are still made aware that it does exist. Instead of seeing a search result, you are presented with a message to log on, sign up for an account, subscribe, or pay a fee in order to view the hidden result. Magnify allows for search results to be modified dynamically at run time based on a combination of the user profile and information returned.
- Multiple Credential Support. Different credentials may be required for authentication when indexing multiple sources of information. After you submit your search, you may be prompted for each required set. Magnify dynamically generates a multi-logon page for each user name and password required. This page can be customized for your site.
- Hide Entire Results. If you do not have access to a search result, it will be hidden from you entirely. There are no indications anywhere in the application to identify that the search result exists. Without authorization, Magnify completely restricts results from being seen.
The main components you must incorporate or configure to implement security for Magnify with Lucene are:
- Security Plug-in. A Java class that you will write to execute your security rules to authenticate Magnify search users and to authorize the content they can view in the returned search results. Developers can use the methods documented in the Magnify Security API Java doc to create a plug-in that authenticates users and authorizes access to the search data based on user credentials.
- WebFOCUS Administration Console Lucene Security Settings. These settings allow you to define the Security plug-in you will be using, and set various parameters related to the Security plug-In.
- Security Plug-in Parameters. These are meta tags added to documents being fed to Lucene and used by the Security plug-in to render the correct search results for a particular user. All the meta tags created in the iWay process flow are available.
Important: When implementing security for Magnify with Lucene, we recommend that you use HTTPS (instead of HTTP) to protect the network transfer of data between systems. However, if the data exists on the same machine as Magnify, the secure protocol is not necessary.
Using Cookie Information to Authenticate
Magnify can verify whether a user has already provided credentials by checking the existence of a cookie. For example, if the user has logged into Managed Reporting, then Magnify can check that the WFC_COOKIE exists and pass this information to the Security plug-in for processing. You can specify the cookie name that Magnify must verify using the Require Cookie parameter in the WebFOCUS Administration Console, as shown in the following image.
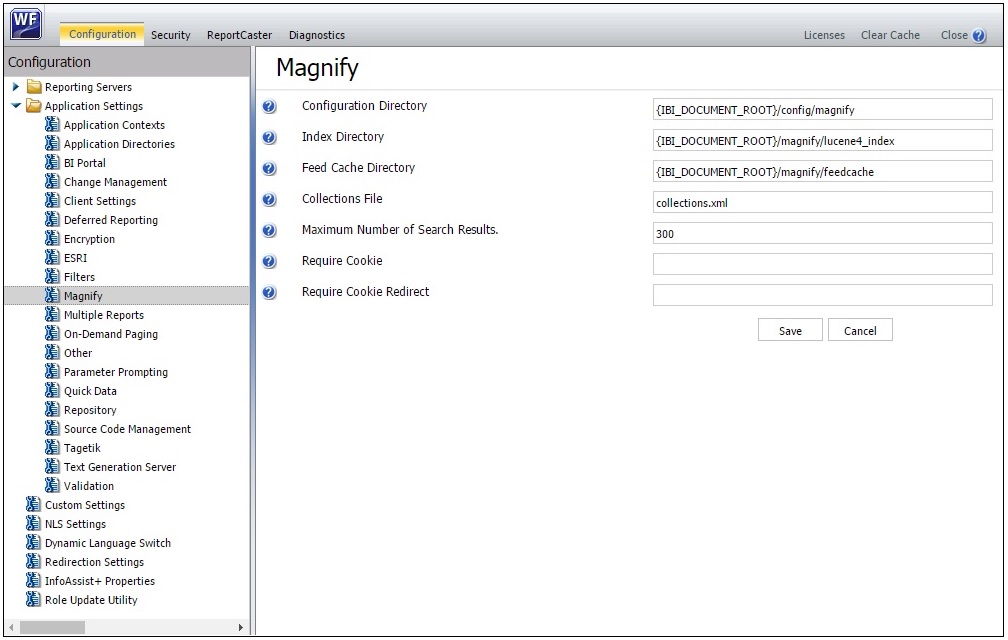
If the cookie does not exist, then Magnify redirects the user to a webpage specified by the Require Cookie Redirect parameter in the WebFOCUS Administration Console. By default, Magnify displays the WebFOCUS home page.
Security API
|
Topics: |
The Magnify Security API is flexible and can integrate with most security models. It provides the framework to authenticate and authorize user access and allows access to HTTP requests, issues alarms of suspicious activity, and sends alerts of erroneous behavior. The Security API Java documentation includes all available functionality and can be accessed using the following URL address:
http://host:[port]/webserver_alias/javadoc/magnify/index.html
where:
- host:[port]
-
Specifies the host and port where WebFOCUS is installed.
- webserver_alias
-
Specifies the web server alias specified during the WebFOCUS installation. The default is ibi_html.
The Magnify Security API Java documentation opens, as shown in the following image.
Writing the Security Plug-In
|
Topics: |
|
How to: |
Magnify secures each search result independently based on user authentication and various authorization levels. By allowing a user the ability to exit Magnify and execute external programs, security rules can be highly customized, scalable, and applied at the most granular control.
Security plug-ins allow for the execution of one program, which can perform stand-alone processing or initiate the execution of another program. The results can then either be passed along and/or evaluated by the Security plug-in and returned to Magnify. This allows Magnify to integrate into your established set of security rules.
Each Security plug-in must be configured using the WebFOCUS Administration Console.
The Security plug-in will:
- Authenticate the user. This
confirms the user identity through some unique piece of information
known only to the user and the authentication system. Though Magnify
does not authenticate its users, this can be done through an authentication
method used in your enterprise. Typically, the authentication information is
a user ID and password that can be verified through a mechanism
such as LDAP, Microsoft Active Directory, or a mainframe system
call. Magnify obtains authentication information in one of the following
ways:
- Browser session. The getUserid() method retrieves the authentication information submitted by the user when prompted for a user ID and password. For an example on authenticating users, see Authenticate Users Using the SimpleSecurity Plug-in.
- WebFOCUS Administration Console parameters. You can pass Magnify the authentication information specified by the Userid and Password parameters using the getSecurityPluginUserid() and getSecurityPluginPassword() methods. These provide administrative access to security information.
- Authorize the requested data. Once the user is authenticated, the plug-in then determines if that user has permission to access the data.
When implementing a Security plug-in for Magnify, the following classes and methods are used:
- run() method. Used to execute the Security plug-in. The run() method is part of the standard Java Development Kit software.
- ibi.search.api.SecurityPlugin interface. Used to implement the Security plug-in Java class specified by the Security Plug-in Name parameter in the WebFOCUS Administration Console. This value must match the value specified by the SECURITY_PLUGIN field in the Lucene index for each record.
- ibi.search.api.SecurityPlugin.getRecords() method. Retrieves the records from the Lucene index. Once the records are retrieved, the Security plug-in must act on each record. For example, the record content can be displayed, hidden, or replaced with a different string.
If you are using any of the e-mail alert features, the following methods may be implemented:
- ibi.search.api.SecurityPluginEnvironment.getSecurityExitEmailNotification(). Retrieves the value of the Notification Email Address(es) parameter in the WebFOCUS Administration Console. This parameter is optional and enables the Security plug-in to notify certain users about special access requirements, possible password attacks, or queries for inappropriate content.
- ibi.search.api.SecurityPluginEnvironment.getSecurityExitemailReplyTo(). Retrieves the value of the Reply to Email Address parameter in the WebFOCUS Administration Console.
- ibi.search.api.SecurityExitEnvironment.getEMailContentType(). Retrieves the e-mail format.
Magnify provides the following Security plug-in samples that illustrate how to implement some of the functionality available in the Magnify Security API:
- ManagedReporting. Authenticates against the Managed Reporting repository to access WebFOCUS reports.
- ReportLibrary. Authenticates against ReportCaster to access information stored in the ReportCaster Library.
- ReturnAllRecords. Illustrates the SECURITY_PLUGIN meta tag that is required when implementing record-level security. This sample plug-in returns records without requiring authentication or authorization.
- LDAPPlugin. Validates a user credentials against an LDAP server and verifies whether the user has access to the group in which the record is assigned.
- SimpleSecurity. Authenticates
users against the magnify_security.xml file.
The ibi.search.securityplugin.SimpleSecurity class enables Magnify to display secure search results based on a user role. The user credentials and role are stored in the following file.
\ibi\WebFOCUSxx\config\magnify\magnify_security.xml
Note: The SimpleSecurity java class is not for production use.
The Security plug-in samples are located in the \ibi\WebFOCUSxx\webapps\webfocus\WEB-INF\classes\ibi\search\securityplugins folder of the WebFOCUS Web application. To compile the samples, Information Builders recommends using JDK 1.6 or higher.
Note: Information Builders offers sample Security plug-ins as a learning tool. Most are not intended for production use. Licensed users are welcome to alter or extend these samples and deploy them in other environments as they see fit. Information Builders will support the documented functionality of its API classes and methods. However, Information Builders is not responsible for functionality or behavior of products built with its API, unless the documented or expected behavior of its discrete classes and methods is different than the actual results.
Lucene Security Settings in WebFOCUS Administration Console
In the Magnify section of the WebFOCUS Administration Console, select Lucene Security.
Select New or Modify to open the Lucene Security Plug-in creation and modification page.
The Lucene security options and parameters are:
- Security Plug-in Name
-
Type a name for the Security plug-in. A Security Plug-in Name binds individual search results to security and provides an alternative name for the Java class name. This field is required and must match the value provided for the SECURITY_PLUGIN field in the index.
- Java Class Name
-
Type a name for the Java class. The Java Class Name is the file name of the Java class assigned to the Security plug-in. The Java class contains functions for authentication, authorization, and alarms. This field is required.
- Realm Information
-
Provide instructions to be displayed in the browser for a search when prompting for a user ID and password. All characters except quotation marks and colons are allowed. This field is required and should provide some detail about the type of data for which the user is accessing. In this way, the user knows which credentials are required. It can also contain a warning message.
- Time to wait for response
-
Type the time limit in milliseconds to wait for a response. The time limit determines how long Magnify waits for a response before timing out for each Security plug-in. The actual wait time is twice the specified time limit because it is applied independently to both authentication and authorization. This field is required, and it must be populated with a positive numeric value. Note that one thousand (1,000) milliseconds is equal to one second.
- Optional parameters
-
Provide a list of optional parameters that can be passed to the Security plug-in. The Optional parameters are command line statements. This field is optional.
- Userid
-
Type a valid user ID. If this field is populated, the user ID is passed to the Security plug-in. This field is optional.
- Password
-
Type a valid password. If this field is populated, the password is passed to the Security plug-in. This field is optional.
- Notification Email Address(es)
-
Provide one or more email addresses to be used for sending notifications based on the results of the security plug-in alarm. Multiple addresses must be separated by a comma or semi-colon. This field is optional.
- Reply to Email Address
-
Provide the email address that notification email recipients can reply to after receiving an email alarm for a Security plug-in. This field is optional.
- Allowed Failures
-
Type the number of failure attempts that must occur before Magnify Search:
- Declares that the Security plug-in experienced a catastrophic failure.
- Stops calling the failed Security plug-in until a retry occurs at a fixed time period.
- Suppresses all of the data that the Security plug-in is responsible for authorizing from the search results.
This field is optional. It must be populated with a positive numeric value when provided.
- Time to wait before retry
-
Type the number of milliseconds that Magnify Search must wait before retrying the Security plug-in after it has failed the number of times set in the Allowed Failures field. The Security plug-in must be successful on the first retry attempt or the specified wait time goes into effect again. This field is optional. It must be populated with a positive numeric value when provided.
Procedure: How to Configure the SimpleSecurity Plug-in Sample
- In the Magnify section of the WebFOCUS Administration Console, select Lucene Security.
- Click New at the bottom of the right pane.
- Type SimpleSecurity in the Security Plug-in Name input box.
- Type ibi.search.securityplugins.SimpleSecurity in the Java Class Name input box.
- Type the
information to display when the user is prompted for credentials
in the Realm Information input box.
The message should provide users with information about the system for which they are providing credentials, since each search record can require authentication to a different system. For example, Enter a valid userid and password to access the Century Electronics employee information.
- Type the
path to the magnify_security.xml file in the Optional
parameters input box as follows:
-passwordfile c:\ibi\WebFOCUS\config\magnify\magnify_security.xml
- Use the
default values for all other configuration parameters. The SimpleSecurity
plug-in sample is now configured.
Syntax: How to Authenticate Users Using the SimpleSecurity Plug-in
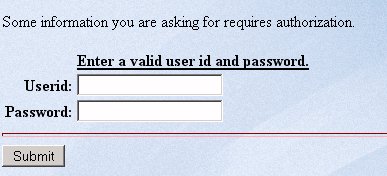
Magnify calls the SimpleSecurity plug-in when a user submits a query to the Magnify search application. Secure records are retrieved from the Lucene index. Users are prompted for a valid user ID and password, as shown in the following image:
The following syntax in the SimpleSecurity plug-in uses the Magnify Security API promptForPassword() method to display the authentication dialog box.
private final void promptForPassword(){
final boolean noAccountCheckbox=this.securitycallback.
getNoAccountCheckbox(this.realmName);
if (!noAccountCheckbox)
{
this.securitycallback.promptForPasswords(this.realmName);
this.securitycallback.
setRealmRequestJSP("search/jsp/passwordPrompt.jsp",
this.realmName);
}
}
The following syntax in the SimpleSecurity plug-in uses the Magnify Security API getUserid() method to retrieve authentication information from the browser session:
public String getUserid(){
return this.userid;
}public void setUserid(String userid)
{
this.userid = userid;
}
The user credentials are then verified against the information stored in the magnify_security.xml file, as follows:
private final boolean isAuthenticated(final String username,
final String password, final String SecurityPluginName_param)
{
final Map <String,NamedNodeMap>
usernameMap = getUserNameMap(SecurityPluginName_param);
if (usernameMap != null && username != null)
{
if (usernameMap.containsKey(username))
{
final NamedNodeMap attMap=usernameMap.get(username);
final Node passwordNode=attMap.getNamedItem("password");
if (passwordNode.getNodeValue().equalsIgnoreCase(password))
{
this.rolesSet=new TreeSet<String>();
final Node rolesNode=attMap.getNamedItem("roles");
final String rolesString=rolesNode.getNodeValue();
if (rolesString != null)
{
final String [] rolesList=rolesString.split(",");
final int nRoles=rolesList.length;
for (int roleIndex=0;roleIndex<nRoles;roleIndex++)
{
this.rolesSet.add(rolesList[roleIndex]);
}
}
return true;
}
}
}
return false;
}| WebFOCUS | |
|
Feedback |