Cross-Site Request Forgery (CSRF)
|
Topics: |
A Cross-Site Request Forgery (CSRF), also known as a one-click attack or session riding, is a type of malicious exploit of a website whereby unauthorized commands are transmitted from a user that the website trusts.
To prevent these types of attacks, WebFOCUS must be configured to use CSRF token protection. Under this configuration, a CSRF token is generated every time the WebFOCUS RESTful Web Services authentication request (IBIRS_action=signOn) is run, and the CSRF token, containing a token name and a token value, is returned within the response.
The CSRF token must be sent as a parameter for any HTTP POST request. Otherwise, a 403 HTTP return code will occur and a CSRF error message will be logged in the websecurity.yyyy-mm-dd.log file.
The CSRF token prevents attacks by providing a value that was generated randomly and then stored in the web session of the actual authenticated user. The client can then check for this value when processing all remaining requests and responses during the session, and can confirm that the request or response is legitimate because it contains the value assigned to that session. Requests or responses that do not contain a CSRF token, or that contain a CSRF token with a name or value that does not match the name or value assigned by the server, are rejected as invalid.
CSRF token protection is supported in Kerberos and SSO environments, but to obtain the delivery of a CSRF token for pre-authenticated users, an explicit IBIRS_action=signOn request that contains the ID of the pre-authenticated user exactly as it appears in the database of the authentication application and no password must be added to the initial sign in transaction. For more information, see Configuring Single Sign On.
CSRF protection is enabled by default in the WebFOCUS Administration Console. To confirm and also view the related settings, on the Configuration tab, under the Application Settings folder, click Filters.
The Filters pane opens, as shown in the following image.

Note that the Cross Site Request Forgery Protection check box is selected.
Obtaining a CSRF Token
The CSRF token is returned in the response of the WebFOCUS RESTful Web Services authentication action (IBIRS_action=signOn), as shown in the following image.
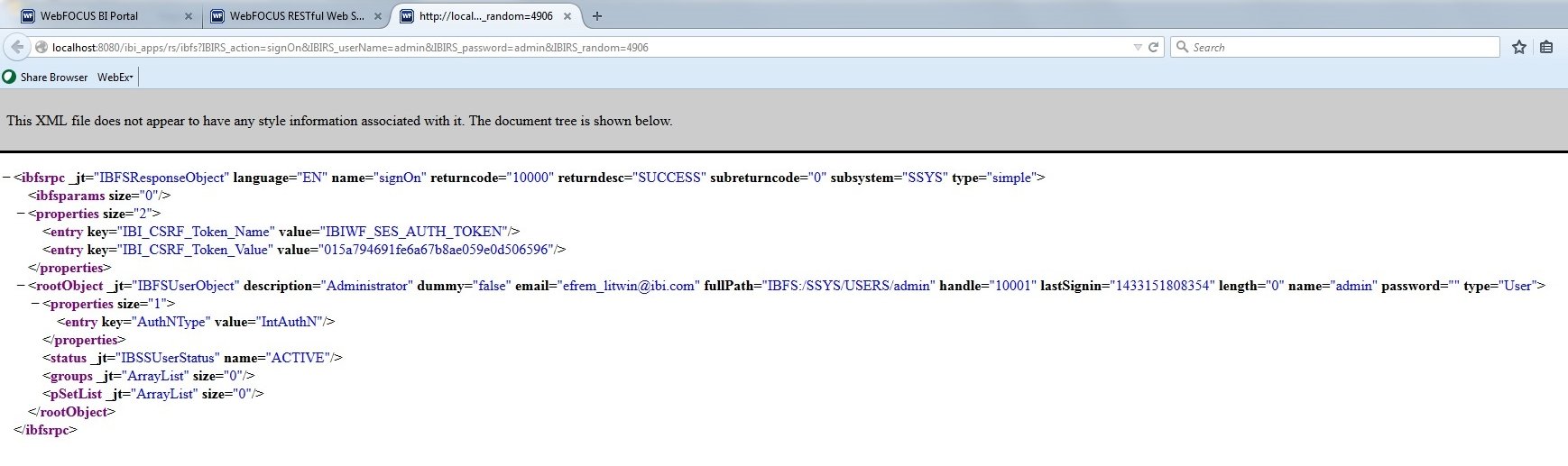
In this example, the name of the CSRF token is IBIWF_SES_AUTH_TOKEN and the value for the CSRF token is 015a794691fe6a67b8ae059e0d506596.
The name of the CSRF token is taken from the value assigned to the Cross Site Request Forgery Security Token (IBI_CSRF_TOKEN_NAME) setting located on the Filters pane of the Administration Console Configuration tab. By default, the value assigned to this setting is IBIWF_SES_AUTH_TOKEN. However, if your configuration assigns a different value to this setting, WebFOCUS returns a different CSRF token name in the response to the sign-in request message.
Passing a CSRF Token
If WebFOCUS is configured to use CSRF token protection, then the CSRF token is passed as a parameter within the body of the POST request for all actions that require a CSRF token.
Example:
The following example shows the WebFOCUS RESTful Web Service request to add a user. This request includes a CSRF token, as shown in the body of the request in the following example.
Post Request URL:
http://localhost:8080/ibi_apps/rs
Body:
IBIRS_path=/SSYS/USERS/testuser&IBIRS_action=put
&IBIRS_object=<object _jt="IBFSUserObject" description="Test Userid" email="restid@informationbuilders.com" password="rest" type="User">
<status _jt="IBSSUserStatus" name="ACTIVE"/>
</object>
&IBIRS_service=ibfs&IBIWF_SES_AUTH_TOKEN=015a794691fe6a67b8ae059e0d506596Typically, the response returns XML code identifying the entry for the new user as shown in the following example.
<ibfsrpc _jt="IBFSResponseObject" language= "en_US" name="put" returncode="10000" returndesc="SUCCCESS" subreturncode="0" type="simple">
<ibfsparams size="5">
<entry key="IBIRS_object" value="****"/>
<entry key="IBIRS_private" value="__null"/>
<entry key="IBIRS_replace" value="true"/>
<entry key="IBIRS_path" value="/SSYS/USERS/testuser"/>
<entry key="IBIRS_args" value="__null"/>
</ibfsparams>
<rootobject _jt="IBFSUserObject" description="Test Userid" dummy="false" email="restid@informationbuilders.com" fullPath="IBFS:/SSYS/USERS/testuser" handle="1784804352" length="0" name="testuser" nameSpace="DB" policy="/+//+8P////30f/e///+/////////v+AAAAA" rsPath="/ibi_apps/rs/ibfs/SSYS/USERS/testuser" thumbPath="/ibi_apps/ibi_html/ibi_images/file_type/unknown.svg" type="User" userStatusDisplay="Active">
<status _jt="IBSSUserStatus" name="ACTIVE"/>
<groups _jt="ArrayList" size="0"/>
<pSetList _jt="ArrayList" size="0"/>
</rootObject>
</ibfsrpc>
However, if the CSRF token is not sent, or if an invalid CSRF token is sent in requests that require a CSRF token, then the following error message will be returned in the response:
<!DOCTYPE HTML> <HTML> <HEAD> <title>403 - Access Denied</title> </HEAD> <body style="background-color:#dae1e7; margin:0;"> <div align="center" style="position:relative;font-family:Arial;top:172px;font-size:25pt;">403 - Access Denied</div> <div align="center" style="position:relative;top:178px;font-size:9pt;font-family:Tahoma;color: #485059;">You are not authorized to view this page</div> </body> </HTML>
| WebFOCUS | |
|
Feedback |