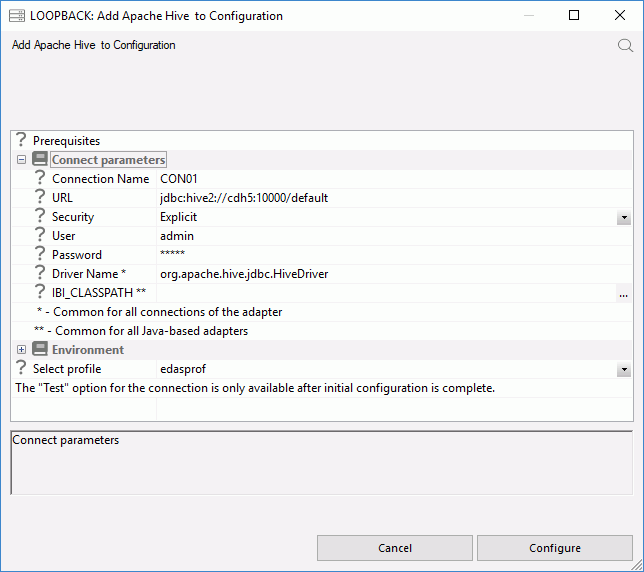
Here are some of the errors you may see when attempting to connect to a Hadoop cluster. These error messages will be prefixed
by FOC1500.
Java listener may be down
ERROR: ncjInit failed. Java listener may be down - see edaprint.log.
This is a Java specific issue. Confirm that your Java version meets your system requirements for bit size (32 bit vs 64 bit),
and that the value for JAVA_HOME is pointing to the correct Java version.
No suitable driver found for jdbc: ...
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: No suitable driver found for jdbc:hive1://server:10000/default
The name of the JDBC driver in the URL is incorrect. For example, in the above URL, the driver is hive1.
ClassNotFoundException
(-1) [00000] JDBFOC>> connectx(): java.lang.ClassNotFoundException:
org.apache.hive.jdbc.HiveDriver
One of the jar files that comprises the Hive JDBC driver is not found in the CLASSPATH, or the driver name is incorrect.
In the above example, the driver name is org.apache.hive.jdbc.HiveDriver.
Required field 'client_protocol' is unset!
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not establish connection to
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: Required field
'client_protocol' is unset! Struct:TOpenSessionReq(client_protocol:null,
configuration:{use:database=default}) This is due to a Java version mismatch. The version of Java on the client is newer than the one on the server. To resolve
this error, update Java on the system where you are running our server.
Could not open client transport with JDBC Uri:
-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not open client transport with JDBC Uri:
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: ...
This is a generic error, and could be
due to any kind of error in the URL or configuration. For more details, read the rest of the message.
Unsupported mechanism type PLAIN
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not open client transport with JDBC Uri:
jdbc:hive2://server:10000/default: Peer indicated failure: Unsupported
mechanism type PLAIN
The cluster has Kerberos enabled and a Kerberos principal to authenticate against is not specified. To resolve this error,
add the following to the end of the URL using your cluster and REALM name:
;principal=hive/server@REALM.COM
UnknownHostException: server
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not open client transport with JDBC Uri:
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: java.net.
UnknownHostException: name
The server you specified could not be reached. Either the system is down or the name is invalid.
Could not open client transport with JDBC Uri:... Connection refused
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not open client transport with JDBC Uri:
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: java.net.
ConnectException: Connection refused: connect
The hostname could be reached, but there is no Hive Thrift server running at the hostname and port number you specified
Client not found in Kerberos database
(-1) [00000] JDBFOC>> makeConnection(): javax.security.auth.login.
LoginException: Client not found in Kerberos database (6)
The user ID (User Principal Name) specified is not a valid Kerberos user ID.
Pre-authentication information was invalid
-1) [00000] JDBFOC>> makeConnection():
javax.security.auth.login.LoginException: Pre-authentication
information was invalid (24)
The user ID (User Principal Name) specified was found, but the password is missing or invalid.
GSS initiate failed
(-1) [00000] JDBFOC>> makeConnection(): conn is NULLjava.sql.
SQLException: Could not open client transport with JDBC Uri:
jdbc:hive2://server:10000/default;principal=hive/server@domain.
COM; GSS initiate failed
Caused by: org.apache.thrift.transport.TTransportException:
Kerberos was unable to authenticate against the specified Service Principal Name.
This occurs if you are using static credentials that were obtained by kinit before the server starts, and did not specify
the option to allow that. To resolve this issue, from the Web Console:
- Click Workspace in the side bar.
- Expand the Java Services folder.
- Right-click DEFAULT.
- Click Properties.
- Expand the JVM Settings section.
- Enter the following in the JVM_OPTIONS box:
-Djava.security.auth.useSubjectCredsOnly=false
This also occurs if you are using subject credentials with explicit or password pass through security, but did not specify
that you are doing so. Add the following to the end of the URL:
;auth=kerberos;kerberosAuthType=fromSubject
Could not create secure connection to ... Failed to open client transport
(0) [ 08S0] Could not create secure connection to
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: Failed to open client
transportjava.sql.SQLException: Could not create secure connection to
jdbc:hive2://server:10000/default;principal=hive/server@REALM.
COM;auth=kerberos;kerberosAuthType=fromSubject: Failed to open client
transport
The client was not able to use Kerberos to connect. You did not enable Kerberos and are using subject credentials. To resolve
this issue, add the following to the server profile:
ENGINE SQLHIV SET ENABLE_KERBEROS ON
Cannot locate default realm
(-1) [00000] JDBFOC>> makeConnection(): javax.security.auth.login.
LoginException: KrbException: Cannot locate default realm
Kerberos looks for the default realm in /etc/krb5.conf, or on Windows krb5.ini, and it either cannot find or read the file
or the default realm is not specified.
For a server running as a service on a Windows machine, you must explicitly specify the realm for the organization and the
KDC. Review the file to make sure that the default realm is specified and correct. To resolve this issue, from the Web Console:
- Click Workspace in the side bar.
- Expand the Java Services folder.
- Right-click DEFAULT.
- Click Properties.
- Expand the JVM Settings section.
- Using the name of your realm and Key Distribution Center (KDC), enter the following in the JVM_OPTIONS box:
-Djava.security.krb5.realm=REALM.COM
-Djava.security.krb5.kdc=kdc.domain.com
Click Save and Restart Java Services.